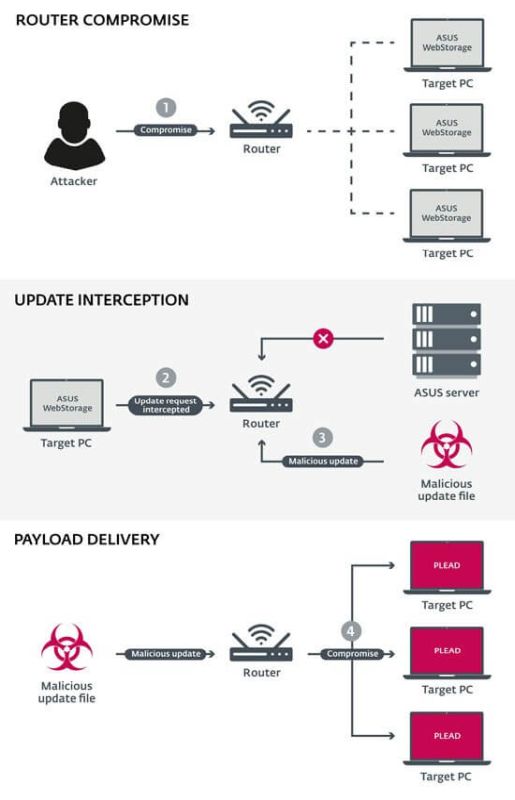
Eset states that BlackTech primarily targets Asian governments and firms. In ASUS’ case, the security research firm detected BlackTech’s activity in Taiwan using router-level Man-in-the-Middle (MitM) attacks, and also where the Plead malware was reportedly most active. Alarms first began ringing when researchers at Eset found a process in WebStorage known as “ASUSWSPPanel.exe” activating Plead. Eset says that the WebStorage software is “vulnerable to these type of attacks” and that “the software doesn’t validate its authenticity before execution”. Once Plead makes its way in, the malware will begin using the compromised routers to further distribute itself, thus allowing BlackTech to remotely access other PC and notebook on a larger scale.
In light of the incident, ASUS says that it has already “took immediate action to mitigate the attack”. By that, the brand means that it shut down the WebStorage update server, which in turn halted BlackTech’s attack. Further action was taken thereafter, with ASUS having revamped the entire host architecture of the ASUS Cloud. (Source: Techspot)