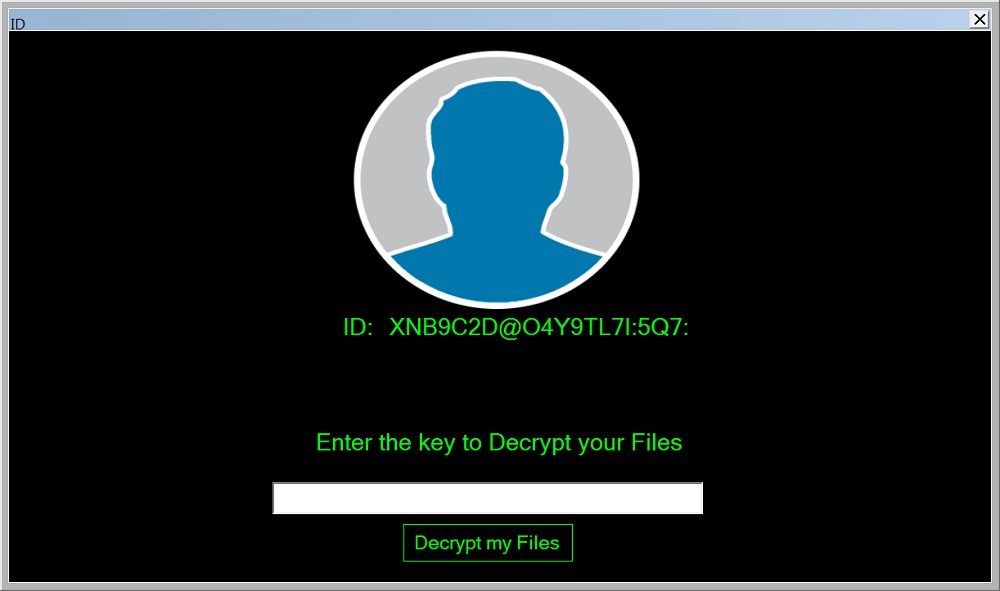
Security company Cyren reports that, upon installation, the ransomware disables Windows Defender and User Account Controls by a registry tweak. Then, it moves the executable file to your startup folder, so that the ransomware runs every time you turn on your PC. It will also monitor your Task Manager to stop you from forcefully terminating its process. And finally, it will infect any USB drives that it detects.
As a ransomware, it encrypts your files and threatens to delete them. This particular one, identified as being of the Hidden-Cry variety, threatens to do so every two hours to instill a sense of urgency. Fortunately, the Cyren researchers claim that it’s possible to decrypt the encrypted files, or even restore deleted ones. At any rate, you shouldn’t be downloading aimbots to begin with. Even if you don’t get one that’s actually malware in disguise, you’ll still be caught by any anti-cheat mechanisms in place. (Source: Cyren via Lifehack)