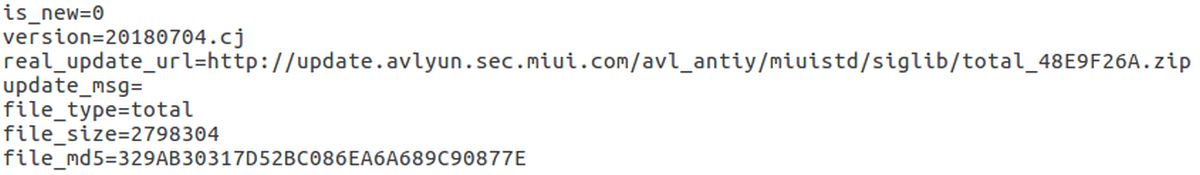
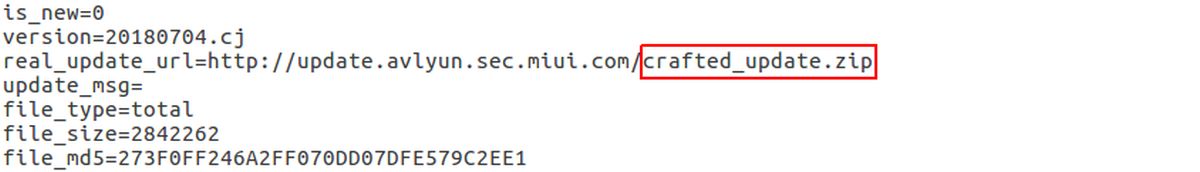
The pre-installed app is called Guard Provider, and contains anti-virus scanners from Avast, AVL and Tencent that serve to detect potential malware. The security flaw found by the researchers lies within the app’s update mechanism.
According to Check Point Research, the security app receives updates through an unsecured HTTP connection. Attackers could take advantage of the Avast Update APK to insert the malware via a man-in-the-middle (MITM) attack. However, the attackers will need to be connected to the same Wi-Fi network as the targeted Xiaomi device. On a relative note, Check Point Research also pointed out the disadvantages of using several SDKs within the same app; because they all share the app context and permissions, a problem in one SDK could very easily compromise the protection of others. Thus, private data on an SDK cannot be isolated therefore can also be accessed by the others.
Xiaomi has already released a patch to fix the security flaw. It’s understandable that users would trust the phone manufacturers’ pre-installed apps, but it’s clear that even they can slip up sometimes. (Source: Android Authority, Check Point Research// Image: Check Point Research)